var q formatfordriverssalarysliponlineU. S. Bureau of Labor Statistics. Couriers and messengers. Pick up and deliver messages, documents, packages, and other items between offices or departments within an establishment or directly to other business concerns, traveling by foot, bicycle, motorcycle, automobile, or public conveyance. Excludes Light Truck or Delivery Services Drivers 5. May 2. 01. 6 median annual wage 2. Projected employment change, 2. Number of new jobs 8,0. Growth rate 8 percent As fast as averageEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. ONET and Career. One. Stop. Dispatchers, except police, fire, and ambulance. Schedule and dispatch workers, work crews, equipment, or service vehicles for conveyance of materials, freight, or passengers, or for normal installation, service, or emergency repairs rendered outside the place of business. Duties may include using radio, telephone, or computer to transmit assignments and compiling statistics and reports on work progress. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 0. Growth rate 0 percent Little or no changeEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Uber and Lyfts efforts to keep drivers from unionizing faced a setback when a federal judge dismissed a lawsuit that would have ended a rideshare driver union in. The Pakistani film Verna begins by portraying a beautiful young woman who is married, welleducated and is building a successful teaching career. How to avoid 6 month labour ban in UAE Dubai, Avoid labor ban in UAE,Ways to avoid six month labour ban in Dubai Abu Dhabi UAE,Avoiding 6 month labor ban. 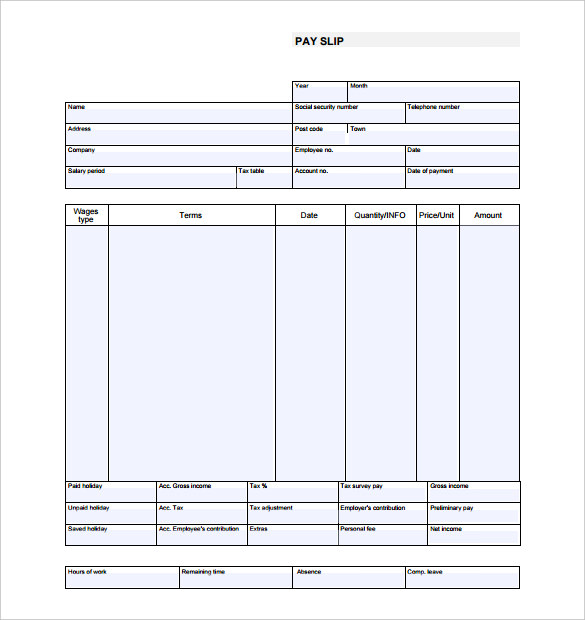 Over time Allowance Rate, Rule,Eligibility, Central government Employees, Railways, Staff Car Driver Under 7th Pay Commission. Life as an employee is not easy and. How to Apply Permanent Family Visa Online. Not a day goes as Saudi government is changing system more simple and online oriented. Now expatriates can easily apply for. I want salary slip format of salary paid in cash. because my last company was a very small so they didnt provide any salary slip of salary in ban. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. The Occupational Outlook Handbook is the governments premier source of career guidance featuring hundreds of occupationssuch as carpenters, teachers, and. Although employment for hundreds of occupations are covered in detail in the Occupational Outlook Handbook, this page presents summary data on additional occupations. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Meter readers, utilities. Read meter and record consumption of electricity, gas, water, or steam. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 1,5. Growth rate 4 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Computer operators. Monitor and control electronic computer and peripheral electronic data processing equipment to process business, scientific, engineering, and other data according to operating instructions. Monitor and respond to operating and error messages. May enter commands at a computer terminal and set controls on computer and peripheral devices. Excludes Computer Occupations 1. Data Entry Keyers 4. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Data entry keyers. Operate data entry device, such as keyboard or photo composing perforator. Duties may include verifying data and preparing materials for printing. Excludes Word Processors and Typists 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 4. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Word processors and typists. Use word processor, computer or typewriter to type letters, reports, forms, or other material from rough draft, corrected copy, or voice recording. May perform other clerical duties as assigned. Excludes Data Entry Keyers 4. Secretaries and Administrative Assistants 4. Court Reporters 2. Medical Transcriptionists 3. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 3. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Mail clerks and mail machine operators, except postal service. Prepare incoming and outgoing mail for distribution. Use hand or mail handling machines to time stamp, open, read, sort, and route incoming mail and address, seal, stamp, fold, stuff, and affix postage to outgoing mail or packages. Duties may also include keeping necessary records and completed forms. May 2. 01. 6 median annual wage 2. Projected employment change, 2. Number of new jobs 7,1. Growth rate 7 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Office machine operators, except computer. Operate one or more of a variety of office machines, such as photocopying, photographic, and duplicating machines, or other office machines. Excludes Computer Operators 4. Mail Clerks and Mail Machine Operators, Except Postal Service 4. Billing and Posting Clerks 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 9,4. Growth rate 1. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Proofreaders and copy markers. Read transcript or proof type setup to detect and mark for correction any grammatical, typographical, or compositional errors. Excludes workers whose primary duty is editing copy. Includes proofreaders of Braille. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 3. Growth rate 2 percent Slower than averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Statistical assistants. Compile and compute data according to statistical formulas for use in statistical studies. May perform actuarial computations and compile charts and graphs for use by actuaries. Includes actuarial clerks. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1,1. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Office and administrative support workers, all other. All office and administrative support workers not listed separately. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education High school diploma or equivalent. One. Stop. First line supervisors of farming, fishing, and forestry workers. Directly supervise and coordinate the activities of agricultural, forestry, aquacultural, and related workers. Excludes First Line Supervisors of Landscaping, Lawn Service, and Groundskeeping Workers 3. Agricultural inspectors. Inspect agricultural commodities, processing equipment, and facilities, and fish and logging operations, to ensure compliance with regulations and laws governing health, quality, and safety. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 7.
Over time Allowance Rate, Rule,Eligibility, Central government Employees, Railways, Staff Car Driver Under 7th Pay Commission. Life as an employee is not easy and. How to Apply Permanent Family Visa Online. Not a day goes as Saudi government is changing system more simple and online oriented. Now expatriates can easily apply for. I want salary slip format of salary paid in cash. because my last company was a very small so they didnt provide any salary slip of salary in ban. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. The Occupational Outlook Handbook is the governments premier source of career guidance featuring hundreds of occupationssuch as carpenters, teachers, and. Although employment for hundreds of occupations are covered in detail in the Occupational Outlook Handbook, this page presents summary data on additional occupations. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Meter readers, utilities. Read meter and record consumption of electricity, gas, water, or steam. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 1,5. Growth rate 4 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Computer operators. Monitor and control electronic computer and peripheral electronic data processing equipment to process business, scientific, engineering, and other data according to operating instructions. Monitor and respond to operating and error messages. May enter commands at a computer terminal and set controls on computer and peripheral devices. Excludes Computer Occupations 1. Data Entry Keyers 4. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Data entry keyers. Operate data entry device, such as keyboard or photo composing perforator. Duties may include verifying data and preparing materials for printing. Excludes Word Processors and Typists 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 4. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Word processors and typists. Use word processor, computer or typewriter to type letters, reports, forms, or other material from rough draft, corrected copy, or voice recording. May perform other clerical duties as assigned. Excludes Data Entry Keyers 4. Secretaries and Administrative Assistants 4. Court Reporters 2. Medical Transcriptionists 3. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 3. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Mail clerks and mail machine operators, except postal service. Prepare incoming and outgoing mail for distribution. Use hand or mail handling machines to time stamp, open, read, sort, and route incoming mail and address, seal, stamp, fold, stuff, and affix postage to outgoing mail or packages. Duties may also include keeping necessary records and completed forms. May 2. 01. 6 median annual wage 2. Projected employment change, 2. Number of new jobs 7,1. Growth rate 7 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Office machine operators, except computer. Operate one or more of a variety of office machines, such as photocopying, photographic, and duplicating machines, or other office machines. Excludes Computer Operators 4. Mail Clerks and Mail Machine Operators, Except Postal Service 4. Billing and Posting Clerks 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 9,4. Growth rate 1. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Proofreaders and copy markers. Read transcript or proof type setup to detect and mark for correction any grammatical, typographical, or compositional errors. Excludes workers whose primary duty is editing copy. Includes proofreaders of Braille. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 3. Growth rate 2 percent Slower than averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Statistical assistants. Compile and compute data according to statistical formulas for use in statistical studies. May perform actuarial computations and compile charts and graphs for use by actuaries. Includes actuarial clerks. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1,1. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Office and administrative support workers, all other. All office and administrative support workers not listed separately. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education High school diploma or equivalent. One. Stop. First line supervisors of farming, fishing, and forestry workers. Directly supervise and coordinate the activities of agricultural, forestry, aquacultural, and related workers. Excludes First Line Supervisors of Landscaping, Lawn Service, and Groundskeeping Workers 3. Agricultural inspectors. Inspect agricultural commodities, processing equipment, and facilities, and fish and logging operations, to ensure compliance with regulations and laws governing health, quality, and safety. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 7.
Read More Pinnacle Game Profiler Use Any Controller with Any PC Game Xbox 3. 60, PS3PS2, Play. Station, PC Gamepads, etc. Maximum Compatibility. If your game controller plugs into a PC, then it works with Pinnacle Game Profiler. Minimum Fuss. Virtually every gamepad is preconfigured for hundreds of games. With Pinnacle just click, download, and play. Add Gamepad or Joystick Support. Want to play a game that doesnt support game controllers No problem. Pinnacle adds support instantly. Modify Your. Games Controls. Controls in your game not working like you want them toChange them with Pinnacle. News, reviews, previews, tips, and downloads for multiple platforms. Pinnacle Game Profiler enables the use of virtually any game controller gamepad, joystick, etc. with any PC game. Its preconfigured for most game titles and.
Pinnacle Game Profiler Use Any Controller with Any PC Game Xbox 3. 60, PS3PS2, Play. Station, PC Gamepads, etc. Maximum Compatibility. If your game controller plugs into a PC, then it works with Pinnacle Game Profiler. Minimum Fuss. Virtually every gamepad is preconfigured for hundreds of games. With Pinnacle just click, download, and play. Add Gamepad or Joystick Support. Want to play a game that doesnt support game controllers No problem. Pinnacle adds support instantly. Modify Your. Games Controls. Controls in your game not working like you want them toChange them with Pinnacle. News, reviews, previews, tips, and downloads for multiple platforms. Pinnacle Game Profiler enables the use of virtually any game controller gamepad, joystick, etc. with any PC game. Its preconfigured for most game titles and.  Realtime problems and outages for Halo. Is the server down Cant log in Here you see what is going on. GameTrailers is your destination to see official trailers first. Powered by IGN, you can expect to see worldfirst exclusive gameplay and the hottest new tra. View and Download JABRA HALO user manual online. HALO Headsets pdf manual download. Browse and play mods created for Star Wars Empire At War at Mod DB. Minecrafts Big Better Together CrossPlay Update Out Now For Xbox One, PC, And Mobile. Xbox One players can now play the sandbox game with those on PC and mobile. Author Nathan Meunierhttp hIDSERP,5344. 1Games Torrents Download Free Games TorrentsDownload Free Games Torrents. Set in the aftermath of its awardwinning predecessor, Sniper Elite 4 continues the series World War Two heritage by transporting. Just because the game designers made a good game doesnt mean you cant make it even better. Or at least different. Game modifications, or mods for short.
Realtime problems and outages for Halo. Is the server down Cant log in Here you see what is going on. GameTrailers is your destination to see official trailers first. Powered by IGN, you can expect to see worldfirst exclusive gameplay and the hottest new tra. View and Download JABRA HALO user manual online. HALO Headsets pdf manual download. Browse and play mods created for Star Wars Empire At War at Mod DB. Minecrafts Big Better Together CrossPlay Update Out Now For Xbox One, PC, And Mobile. Xbox One players can now play the sandbox game with those on PC and mobile. Author Nathan Meunierhttp hIDSERP,5344. 1Games Torrents Download Free Games TorrentsDownload Free Games Torrents. Set in the aftermath of its awardwinning predecessor, Sniper Elite 4 continues the series World War Two heritage by transporting. Just because the game designers made a good game doesnt mean you cant make it even better. Or at least different. Game modifications, or mods for short. 

 All it takes are a few soft taps to her face to awaken her. Jane looks over her situation but shes still stoic, unafraid. JJ uses a scissors to slice off her panties and stuffs them in her mouth to gag her, taking the same rope thats looped around her neck and putting it across her mouth to hold the gag in place, not nearly as effective as using a new rope and wrapping that around her head. JJ then takes bare electrical wire and tapes the ends to her temples nice touch and also to her nipples and her pussy.
All it takes are a few soft taps to her face to awaken her. Jane looks over her situation but shes still stoic, unafraid. JJ uses a scissors to slice off her panties and stuffs them in her mouth to gag her, taking the same rope thats looped around her neck and putting it across her mouth to hold the gag in place, not nearly as effective as using a new rope and wrapping that around her head. JJ then takes bare electrical wire and tapes the ends to her temples nice touch and also to her nipples and her pussy. -1483494065.jpg)
 And how does Jane react She tells JJ fuck you through her gag, more unwanted feistiness when she should be panicky and crying. And so. its Shocky TimeWhat follows is a better than average electrical torture scene. Although no screaming here, its quite effective, with Janes body stiffening with every jolt. When hes done with her, JJ removes the wires and gag and takes full advantage of her by raping Janes pussy. According to Jane, the rape was supposed to be simulated but he couldnt help himself and did it to her for real. Well, can you blame himShe looks incredibly hot in that position. And as he thrusts himself into her, the rope around Janes neck tightens up, so shes being choked while shes being raped. This time, Jane reacts a bit more noisily until she finally passes out. Then its more Unconscious Jane as she is untied, stripped completely and re tied in a standing position with her arms over her head. For once, her wake up call is more than just a few soft taps to the face. JJ gets her attention by giving her several blows with his whip, and continues whipping her for several minutes until there are bloody slash marks up and down the back of her body. Jane ties to kick back at her attacker but its all in vain. He keeps whipping her until well past the time that shes. This enables JJ to bind Unconscious Jane upside down to a wooden ladder, with her knees bent over the upper rung and her hands tied behind her, sort of a loose hogtie. Its a pretty inventive position, one I havent seen before. JJ wakes her up by softly tapping her face he must have a real magic touch. And the torture this time is also pretty unique. He takes a bucket filled with water and raises it up to Janes head so that she experiences a drowning torture while tied in this helpless position. After the bucket is removed, Jane pleads, coughs and begs him to stop while gasping for air. She is clearly not acting here and thats why the scene is so effective. He uses the bucket on her several times, and on the last one she is kept under water for quite a while, until it is mercifully removed and she hangs silently, still breathing but unconscious. Quick, JJ, softly tap her face so she can move again Several excruciatingly slow minutes later, JJ has finally tied Jane into a new position pretty convenient that shes unconscious every time so that he can bind her with no distractions, isnt it. This one is worth waiting for. Jane is now standing on her tiptoes, leaning against a post with her arms tied far apart to a bar over her head, leaving her stretched out and vulnerable. Then he worsens her predicament by tying her ankles apart with a spreader bar. There are several instances where Jane is hanging suspended as JJ cuts into her with his whip, and this scene is a lot more fun since we get to see Janes pretty face as she reacts in anguish to every blow. Once shes unconscious again, Jane hangs limply in her bonds, her front side now stained with lots and lots of bloody marks, which seems only fair since her backside got marked up earlier. JJ drags her limp body over to the wall for one more torture, and this one will be the worst of all for her. He chains her with her arms tied to the wall over her head and. Works every time. JJ gets right in front of Jane and holds up 4 sinister looking spikes and a hammering tool to her face. Guess what JJ tells her. I dont need a confession any more. This is not to make you talk. This is just for me. Jane starts crying, but he is undeterred. He takes her left leg and proceeds to hammer one of the spikes through her ankle and into a wooden peg that is bolted next to the wall. Jane wails in agony as he continues on, impaling the other ankle to the other side. He doesnt stop until both of Janes wrists are then spread apart and hammered into the wall, impaling her to the wall so that her body now resembles the letter X. JJ later tortures both her breasts with by stabbing them with another spike, as if she wasnt already in enough pain. He pulls up a chair, takes a swig of beer and watches Jane slowly suffer. It takes a long time, but she eventually slumps her head and expires, now just a pretty victim of crucifixion. And no amount of soft tapping to her face is going to bring her back this time. My reaction to this film is easy to gauge. When Jane is awake, theres lots of good suffering. But when shes knocked out. Way too much Unconscious Jane. Ive never been a fan of the sleepy girl fetish.
And how does Jane react She tells JJ fuck you through her gag, more unwanted feistiness when she should be panicky and crying. And so. its Shocky TimeWhat follows is a better than average electrical torture scene. Although no screaming here, its quite effective, with Janes body stiffening with every jolt. When hes done with her, JJ removes the wires and gag and takes full advantage of her by raping Janes pussy. According to Jane, the rape was supposed to be simulated but he couldnt help himself and did it to her for real. Well, can you blame himShe looks incredibly hot in that position. And as he thrusts himself into her, the rope around Janes neck tightens up, so shes being choked while shes being raped. This time, Jane reacts a bit more noisily until she finally passes out. Then its more Unconscious Jane as she is untied, stripped completely and re tied in a standing position with her arms over her head. For once, her wake up call is more than just a few soft taps to the face. JJ gets her attention by giving her several blows with his whip, and continues whipping her for several minutes until there are bloody slash marks up and down the back of her body. Jane ties to kick back at her attacker but its all in vain. He keeps whipping her until well past the time that shes. This enables JJ to bind Unconscious Jane upside down to a wooden ladder, with her knees bent over the upper rung and her hands tied behind her, sort of a loose hogtie. Its a pretty inventive position, one I havent seen before. JJ wakes her up by softly tapping her face he must have a real magic touch. And the torture this time is also pretty unique. He takes a bucket filled with water and raises it up to Janes head so that she experiences a drowning torture while tied in this helpless position. After the bucket is removed, Jane pleads, coughs and begs him to stop while gasping for air. She is clearly not acting here and thats why the scene is so effective. He uses the bucket on her several times, and on the last one she is kept under water for quite a while, until it is mercifully removed and she hangs silently, still breathing but unconscious. Quick, JJ, softly tap her face so she can move again Several excruciatingly slow minutes later, JJ has finally tied Jane into a new position pretty convenient that shes unconscious every time so that he can bind her with no distractions, isnt it. This one is worth waiting for. Jane is now standing on her tiptoes, leaning against a post with her arms tied far apart to a bar over her head, leaving her stretched out and vulnerable. Then he worsens her predicament by tying her ankles apart with a spreader bar. There are several instances where Jane is hanging suspended as JJ cuts into her with his whip, and this scene is a lot more fun since we get to see Janes pretty face as she reacts in anguish to every blow. Once shes unconscious again, Jane hangs limply in her bonds, her front side now stained with lots and lots of bloody marks, which seems only fair since her backside got marked up earlier. JJ drags her limp body over to the wall for one more torture, and this one will be the worst of all for her. He chains her with her arms tied to the wall over her head and. Works every time. JJ gets right in front of Jane and holds up 4 sinister looking spikes and a hammering tool to her face. Guess what JJ tells her. I dont need a confession any more. This is not to make you talk. This is just for me. Jane starts crying, but he is undeterred. He takes her left leg and proceeds to hammer one of the spikes through her ankle and into a wooden peg that is bolted next to the wall. Jane wails in agony as he continues on, impaling the other ankle to the other side. He doesnt stop until both of Janes wrists are then spread apart and hammered into the wall, impaling her to the wall so that her body now resembles the letter X. JJ later tortures both her breasts with by stabbing them with another spike, as if she wasnt already in enough pain. He pulls up a chair, takes a swig of beer and watches Jane slowly suffer. It takes a long time, but she eventually slumps her head and expires, now just a pretty victim of crucifixion. And no amount of soft tapping to her face is going to bring her back this time. My reaction to this film is easy to gauge. When Jane is awake, theres lots of good suffering. But when shes knocked out. Way too much Unconscious Jane. Ive never been a fan of the sleepy girl fetish. 
 Scientists, Artists, and Smash Mouth Tell Us What Music Theyd Send Into Deep Space. On August 2. 0th, 1. NASA launched its Voyager 2 spacecraft from Cape Canaveral, Florida. It followed up with the launch of Voyager 1 just a few weeks later on September 5th. Over the course of their careers, both spacecraft have explored gas giants and their moons, the Kuiper Belt and more, constantly pushing the boundaries of what science and humanity are capable of. Voyager 1 and 2 both carry a special trinket known as The Golden Record. The 1. 2 inch, gold plated copper phonograph records contains a variety of sounds and music selected by astronomer Carl Sagan and his colleagues. The Golden Record was intended to serve as a greeting for any alien life forms who found itan encapsulation of the human experience through sound.
Scientists, Artists, and Smash Mouth Tell Us What Music Theyd Send Into Deep Space. On August 2. 0th, 1. NASA launched its Voyager 2 spacecraft from Cape Canaveral, Florida. It followed up with the launch of Voyager 1 just a few weeks later on September 5th. Over the course of their careers, both spacecraft have explored gas giants and their moons, the Kuiper Belt and more, constantly pushing the boundaries of what science and humanity are capable of. Voyager 1 and 2 both carry a special trinket known as The Golden Record. The 1. 2 inch, gold plated copper phonograph records contains a variety of sounds and music selected by astronomer Carl Sagan and his colleagues. The Golden Record was intended to serve as a greeting for any alien life forms who found itan encapsulation of the human experience through sound.  While its extremely unlikely that any intelligent life would stumble across a record hurtling through our random corner of spaceor have the equipment to play itits comforting that a piece of humanity is pressing on, somewhere out there in the void. In honor of the 4. Voyager missions, we asked astronomers and space savvy musicians to tell us what music theyd send if NASA hypothetically launched another Golden Record. Some have proposed that NASA beam out a digital Golden Record 2. New Horizons spacecraft in 2. Regrettably, Pitbull did not respond to Gizmodos multiple requests for commentbut these other responses are still very good Michelle Zauner. Philadelphia based musician, Japanese Breakfast outer space electro pop enthusiast. Songs I cant choose one Michael Jackson song. Aint No Mountain High by Marvin Gaye and Tammi Terrell, Mariah Carey, Fantasy, Whitney Houston, I Will Always Love You, Slowdive, Souvlaki Space Station, Bjork, Bachelorette, Kate Bush, Running Up That Hill. Sounds The ocean, rushing water, wind through leaves, Beyonc singing a capella in her dressing room, Stevie Nicks singing a capella in her dressing room, Mariah Careys whistle tone compilation. Matt Russo. Postdoctoral researcher at the Canadian Institute for Theoretical Astrophysics, musician, co founder System SoundsSongs Here comes the sun by The Beatles. Sagan pushed for this to be included on the first Golden Record but EMI held the copyright and refused. Its time to set things right again. Sounds The most self promotional suggestion possible my own sonification of the TRAPPIST 1 planetary system, which shows the connections between orbital dynamics which aliens are surly pros at and the music contained on the record. Id be especially interested in some feedback from the music critics from TRAPPIST 1 but I may not be around long enough to receive it. Also, the gravitational waves emitted by merging black holes, converted into sound. Id imagine that aliens find black holes just as fascinating as we do so lets let them know were hip to the good stuff. Doug Vakoch. Astronomer and president of METI International, an organization that searches for radio signals from advanced extraterrestrial life. As a NASA mission, its understandable that musical selections from the Western classical tradition and the United States were given preference. In a 2. 01. 7 redo, though, we should be more globally inclusive. Rather than trying to get copyright permission for including Sgt. Peppers Lonely Hearts Club Band, a request the Beatles turned down in the 1. Golden record. After all, the Beatles have already been sent into space, thanks to NASAs 2. Across the Universe to Polaris, the North Star, to celebrate the agencys 5. Ethan Hein. Doctoral fellow in music education at NYU, adjunct professor of music technology at NYU and Montclair State university, musicianI would probably just cast Thriller in gold and send that. Smash Mouth. Grammy nominated recording artists and noted Sun walking enthusiasts.
While its extremely unlikely that any intelligent life would stumble across a record hurtling through our random corner of spaceor have the equipment to play itits comforting that a piece of humanity is pressing on, somewhere out there in the void. In honor of the 4. Voyager missions, we asked astronomers and space savvy musicians to tell us what music theyd send if NASA hypothetically launched another Golden Record. Some have proposed that NASA beam out a digital Golden Record 2. New Horizons spacecraft in 2. Regrettably, Pitbull did not respond to Gizmodos multiple requests for commentbut these other responses are still very good Michelle Zauner. Philadelphia based musician, Japanese Breakfast outer space electro pop enthusiast. Songs I cant choose one Michael Jackson song. Aint No Mountain High by Marvin Gaye and Tammi Terrell, Mariah Carey, Fantasy, Whitney Houston, I Will Always Love You, Slowdive, Souvlaki Space Station, Bjork, Bachelorette, Kate Bush, Running Up That Hill. Sounds The ocean, rushing water, wind through leaves, Beyonc singing a capella in her dressing room, Stevie Nicks singing a capella in her dressing room, Mariah Careys whistle tone compilation. Matt Russo. Postdoctoral researcher at the Canadian Institute for Theoretical Astrophysics, musician, co founder System SoundsSongs Here comes the sun by The Beatles. Sagan pushed for this to be included on the first Golden Record but EMI held the copyright and refused. Its time to set things right again. Sounds The most self promotional suggestion possible my own sonification of the TRAPPIST 1 planetary system, which shows the connections between orbital dynamics which aliens are surly pros at and the music contained on the record. Id be especially interested in some feedback from the music critics from TRAPPIST 1 but I may not be around long enough to receive it. Also, the gravitational waves emitted by merging black holes, converted into sound. Id imagine that aliens find black holes just as fascinating as we do so lets let them know were hip to the good stuff. Doug Vakoch. Astronomer and president of METI International, an organization that searches for radio signals from advanced extraterrestrial life. As a NASA mission, its understandable that musical selections from the Western classical tradition and the United States were given preference. In a 2. 01. 7 redo, though, we should be more globally inclusive. Rather than trying to get copyright permission for including Sgt. Peppers Lonely Hearts Club Band, a request the Beatles turned down in the 1. Golden record. After all, the Beatles have already been sent into space, thanks to NASAs 2. Across the Universe to Polaris, the North Star, to celebrate the agencys 5. Ethan Hein. Doctoral fellow in music education at NYU, adjunct professor of music technology at NYU and Montclair State university, musicianI would probably just cast Thriller in gold and send that. Smash Mouth. Grammy nominated recording artists and noted Sun walking enthusiasts.  A rep for the band told Gizmodo They said, All Star and Walkin On The Sun of course.
A rep for the band told Gizmodo They said, All Star and Walkin On The Sun of course. 
 Cryptostorm Iceland, 1. HIDEme Malaysia, 8. Nord. VPN Panama, 5. Perfect Privacy Panama, 4. Privatoria Czech Republic, 1. One VPN provider attracted my attention particularily, that being Boleh. VPN, since it is one of the only two providers that offers Tor to VPN alongside VPN to Tor the other one being Air. VPN, which is based in Italy, therefore part of 1. Make sure to check the VPN providers canary. It is a document that confirms that the VPN provider was not touched by the government. It should be updated every month, if it isnt unsubscribe. Example. How to increase VPN security. Pay with untraceable money. Sign up for an anonymous e mail account using Tor and use a Bitcoin Mixer to send Bitcoins to a newly generated address in your local wallet. Alternatively, use the Bitcoin OTC to purchase Bitcoins over the counter from a person, rather than an exchange. Then, use a patched Bitcoin client, such as coderrrs anonymity patch to avoid linking the newly generated address to any of your pre existing Bitcoin addresses. Andrew, Private Internet Access. Make sure you dont disconnect from VPN and prevent DNS leaks. Use the pro version of VPNCheck to automatically disconnect from internet when losing connection to VPN and to prevent DNS leaks. Or search for the manual way of doing it. Use multiple VPNs. Another measure to consider is using two or more VPNs. Basically activate one VPN first, then another one, done. Resolve the PPTP IPv. VPN flaw. Not likely to affect everyone. PPTP is the weakest VPN protocol and if you use one of the VPNs I mentioned before you will likely use a better protocol, but for those who do, there is a possible flaw that you can correct like thisfor Windows Vista and above Open cmd prompt and type netsh interface teredo set state disabled. Secure your router. Heres a guide. 2. Install an antivirus. There are three tiers of antiviruses antivirus sofwtare, internet suite and premium security suites. Read about them here. At minimum use Microsoft Security Essentials free software from Microsoft, though paid antiviruses such as Bitdefender, Kaspersky, etc. are better. Use Tor and Tails. OS for safe web browsing. Many popular browsers are not highest ranked in regards to keeping your anonymity. For example, while Chrome is theoretically secure from spyware and adware, their stance on privacy can be summarized as follows He went on, speaking about the future of search. With your permission you give us more information about you, about your friends, and we can improve the quality of our searches. We dont need you to type at all. We know where you are. We know where youve been. We can more or less know what youre thinking about. There are factors one must be careful of cookies, encryption https, tracking ads, javascript exploits, canvas fingerprinting and others. A writeup on these would take a long time so research them on your own if you wish. I will just mention browsers that avoids these issues. Use safe search engine. Instead of using the google search engine use disconnect. Tor or install as extension into FirefoxTor Browser. Tor Browser is an internet browser designed for online anonymity. It is a modified version of Firefox with add ons pre installed. Tor works somewhat similar to the VPN concept. Before connecting to a website you go through nodes. Which are private stations, each with its own IP. So instead of showing your IP, it will show the IP of the last node you traveled through. The downside of Tor is that it is slow, due to the fact that it works thanks to enthusiastic individuals. Tor is not for casual usage, but specifically for privacy needs, particularly posting online or searching the deep web. Tor has some weaknesses you must be aware of First. Oftentimes when you are using a network, the network provider cant see what you are browsing, but they can see that you are using Tor. You can use things like a bridge obfuscator, obfsproxy, or setting VPN to Tor. This is a complex issue, here is a guide on hiding tor usage from ISP internet service provider. Second. The trustworthiness of exit relays. When the government found out about the popularity of Tor they created their own exit nodes, that acted as honey traps. To fight this, use a Tails. OS or booted off a flash stick, DVD or SD card in a public wifi spot, like a coffee shop. That way even if the final node was a trap, it would only lead to your Tails. OS profile, not your general one. Check so the public wifi spot you are using has no cameras around, so they will not be able to check camera footage of who used a laptop in that particular time frame. Dont forget to log off when finished. Alternatively, use Tor to VPN. Third. Often many programs, like torrents, will ignore Tor, even if you manually force them and just connect straight away, thus giving you away. The answer is to not use torrents with Tor. I REPEAT, NO FILE SHARING ON TOR. There are of course othervariousvulnerabilities out there. And as a reminder, Silk Road, a large black market was cracked in the past. Combining Tor with a VPNTor is good on its own but even better when combined with a VPN. There are 2 methods Tor to VPN, VPN to Tor. Both have their weaknesses. First one allows ISPs to see you use Tor, the second does not protect from malicious end relays. VPN to Tormasks your Tor usage, Tor to VPN protects from malicious exit nodes. Store share your files with uploaded. Learn more about our services videoAfter entering your e. Mail addres and receipt of your registration youll simultaneously receive your personal access data from us. This is always free of charge.
Cryptostorm Iceland, 1. HIDEme Malaysia, 8. Nord. VPN Panama, 5. Perfect Privacy Panama, 4. Privatoria Czech Republic, 1. One VPN provider attracted my attention particularily, that being Boleh. VPN, since it is one of the only two providers that offers Tor to VPN alongside VPN to Tor the other one being Air. VPN, which is based in Italy, therefore part of 1. Make sure to check the VPN providers canary. It is a document that confirms that the VPN provider was not touched by the government. It should be updated every month, if it isnt unsubscribe. Example. How to increase VPN security. Pay with untraceable money. Sign up for an anonymous e mail account using Tor and use a Bitcoin Mixer to send Bitcoins to a newly generated address in your local wallet. Alternatively, use the Bitcoin OTC to purchase Bitcoins over the counter from a person, rather than an exchange. Then, use a patched Bitcoin client, such as coderrrs anonymity patch to avoid linking the newly generated address to any of your pre existing Bitcoin addresses. Andrew, Private Internet Access. Make sure you dont disconnect from VPN and prevent DNS leaks. Use the pro version of VPNCheck to automatically disconnect from internet when losing connection to VPN and to prevent DNS leaks. Or search for the manual way of doing it. Use multiple VPNs. Another measure to consider is using two or more VPNs. Basically activate one VPN first, then another one, done. Resolve the PPTP IPv. VPN flaw. Not likely to affect everyone. PPTP is the weakest VPN protocol and if you use one of the VPNs I mentioned before you will likely use a better protocol, but for those who do, there is a possible flaw that you can correct like thisfor Windows Vista and above Open cmd prompt and type netsh interface teredo set state disabled. Secure your router. Heres a guide. 2. Install an antivirus. There are three tiers of antiviruses antivirus sofwtare, internet suite and premium security suites. Read about them here. At minimum use Microsoft Security Essentials free software from Microsoft, though paid antiviruses such as Bitdefender, Kaspersky, etc. are better. Use Tor and Tails. OS for safe web browsing. Many popular browsers are not highest ranked in regards to keeping your anonymity. For example, while Chrome is theoretically secure from spyware and adware, their stance on privacy can be summarized as follows He went on, speaking about the future of search. With your permission you give us more information about you, about your friends, and we can improve the quality of our searches. We dont need you to type at all. We know where you are. We know where youve been. We can more or less know what youre thinking about. There are factors one must be careful of cookies, encryption https, tracking ads, javascript exploits, canvas fingerprinting and others. A writeup on these would take a long time so research them on your own if you wish. I will just mention browsers that avoids these issues. Use safe search engine. Instead of using the google search engine use disconnect. Tor or install as extension into FirefoxTor Browser. Tor Browser is an internet browser designed for online anonymity. It is a modified version of Firefox with add ons pre installed. Tor works somewhat similar to the VPN concept. Before connecting to a website you go through nodes. Which are private stations, each with its own IP. So instead of showing your IP, it will show the IP of the last node you traveled through. The downside of Tor is that it is slow, due to the fact that it works thanks to enthusiastic individuals. Tor is not for casual usage, but specifically for privacy needs, particularly posting online or searching the deep web. Tor has some weaknesses you must be aware of First. Oftentimes when you are using a network, the network provider cant see what you are browsing, but they can see that you are using Tor. You can use things like a bridge obfuscator, obfsproxy, or setting VPN to Tor. This is a complex issue, here is a guide on hiding tor usage from ISP internet service provider. Second. The trustworthiness of exit relays. When the government found out about the popularity of Tor they created their own exit nodes, that acted as honey traps. To fight this, use a Tails. OS or booted off a flash stick, DVD or SD card in a public wifi spot, like a coffee shop. That way even if the final node was a trap, it would only lead to your Tails. OS profile, not your general one. Check so the public wifi spot you are using has no cameras around, so they will not be able to check camera footage of who used a laptop in that particular time frame. Dont forget to log off when finished. Alternatively, use Tor to VPN. Third. Often many programs, like torrents, will ignore Tor, even if you manually force them and just connect straight away, thus giving you away. The answer is to not use torrents with Tor. I REPEAT, NO FILE SHARING ON TOR. There are of course othervariousvulnerabilities out there. And as a reminder, Silk Road, a large black market was cracked in the past. Combining Tor with a VPNTor is good on its own but even better when combined with a VPN. There are 2 methods Tor to VPN, VPN to Tor. Both have their weaknesses. First one allows ISPs to see you use Tor, the second does not protect from malicious end relays. VPN to Tormasks your Tor usage, Tor to VPN protects from malicious exit nodes. Store share your files with uploaded. Learn more about our services videoAfter entering your e. Mail addres and receipt of your registration youll simultaneously receive your personal access data from us. This is always free of charge. 


 Download game PS3 iso, game RPCS3, game PC, Direct Links PS3 RPCS3, Torrent PS3 RPCS3, DLC PS3 RPCS3, Google drive game PS3 RPCS3 PC. CoolROM. coms game information and ROM ISO download page for WWE SmackDown Here Comes the Pain Sony Playstation 2. CoolROM. coms game information and ROM ISO download page for WWE SmackDown vs. RAW 2011 Sony Playstation Portable. Android Apps, Games, Themes, Highly Compressed PSPPPSSPP Games, Tricks, Offers And Many Other Good Stuff For Free. Mediafire 100 working download link WWE 2K17 PPSSPP ISO Crash Fix Download link how to download and install step by step easy. PSPshare ultimate PSP Game download source. Download free psp game ISO. Free PSP ISO,CSO,ROM Games Download. Best and the Latest PSP games downloads. heres the solution to the biggest problem of ppsspp psp emulator on android Game tested WWE Smackdown vs Raw 2008 Link for PPSSPP v0. 9. 9. 1 http.
Download game PS3 iso, game RPCS3, game PC, Direct Links PS3 RPCS3, Torrent PS3 RPCS3, DLC PS3 RPCS3, Google drive game PS3 RPCS3 PC. CoolROM. coms game information and ROM ISO download page for WWE SmackDown Here Comes the Pain Sony Playstation 2. CoolROM. coms game information and ROM ISO download page for WWE SmackDown vs. RAW 2011 Sony Playstation Portable. Android Apps, Games, Themes, Highly Compressed PSPPPSSPP Games, Tricks, Offers And Many Other Good Stuff For Free. Mediafire 100 working download link WWE 2K17 PPSSPP ISO Crash Fix Download link how to download and install step by step easy. PSPshare ultimate PSP Game download source. Download free psp game ISO. Free PSP ISO,CSO,ROM Games Download. Best and the Latest PSP games downloads. heres the solution to the biggest problem of ppsspp psp emulator on android Game tested WWE Smackdown vs Raw 2008 Link for PPSSPP v0. 9. 9. 1 http.  Free Download 200 mb ppsspp games Full Version, Descargar 200 mb ppsspp games Gratis, Download 200 mb ppsspp games Latest version. Download game ps3 iso, hack game ps3 iso, LEGO Marvel Super Heroes ps3 iso, game ps, game ps3 free, download game ps3 mediafire, google drive.
Free Download 200 mb ppsspp games Full Version, Descargar 200 mb ppsspp games Gratis, Download 200 mb ppsspp games Latest version. Download game ps3 iso, hack game ps3 iso, LEGO Marvel Super Heroes ps3 iso, game ps, game ps3 free, download game ps3 mediafire, google drive. 

 Gaussian elimination Wikipedia. In linear algebra, Gaussian elimination also known as row reduction is an algorithm for solving systems of linear equations. It is usually understood as a sequence of operations performed on the corresponding matrix of coefficients. This method can also be used to find the rank of a matrix, to calculate the determinant of a matrix, and to calculate the inverse of an invertible square matrix. I have to tell you about the Kalman filter, because what it does is pretty damn amazing. Surprisingly few software engineers and scientists seem to know about it, and. To freeze bond, go to Edit Redundant Coordinates Specify your bond you need to freeze. All in gaussian view. The method is named after Carl Friedrich Gauss 1. Chinese mathematicians as early as 1. CE see History section. To perform row reduction on a matrix, one uses a sequence of elementary row operations to modify the matrix until the lower left hand corner of the matrix is filled with zeros, as much as possible. There are three types of elementary row operations 1 Swapping two rows, 2 Multiplying a row by a non zero number, 3 Adding a multiple of one row to another row. Using these operations, a matrix can always be transformed into an upper triangular matrix, and in fact one that is in row echelon form. Once all of the leading coefficients the left most non zero entry in each row are 1, and every column containing a leading coefficient has zeros elsewhere, the matrix is said to be in reduced row echelon form. Simulation of Digital Communication Systems Using Matlab eBook Author Mathuranathan Viswanathan Published Feb. 18, 2013 Language English ISBN 9781301525089. A renewed and restyled version of the CRYSTAL Tutorials web site is now available online. Tutorials have been also updated to cover the new features of CRYSTAL17.
Gaussian elimination Wikipedia. In linear algebra, Gaussian elimination also known as row reduction is an algorithm for solving systems of linear equations. It is usually understood as a sequence of operations performed on the corresponding matrix of coefficients. This method can also be used to find the rank of a matrix, to calculate the determinant of a matrix, and to calculate the inverse of an invertible square matrix. I have to tell you about the Kalman filter, because what it does is pretty damn amazing. Surprisingly few software engineers and scientists seem to know about it, and. To freeze bond, go to Edit Redundant Coordinates Specify your bond you need to freeze. All in gaussian view. The method is named after Carl Friedrich Gauss 1. Chinese mathematicians as early as 1. CE see History section. To perform row reduction on a matrix, one uses a sequence of elementary row operations to modify the matrix until the lower left hand corner of the matrix is filled with zeros, as much as possible. There are three types of elementary row operations 1 Swapping two rows, 2 Multiplying a row by a non zero number, 3 Adding a multiple of one row to another row. Using these operations, a matrix can always be transformed into an upper triangular matrix, and in fact one that is in row echelon form. Once all of the leading coefficients the left most non zero entry in each row are 1, and every column containing a leading coefficient has zeros elsewhere, the matrix is said to be in reduced row echelon form. Simulation of Digital Communication Systems Using Matlab eBook Author Mathuranathan Viswanathan Published Feb. 18, 2013 Language English ISBN 9781301525089. A renewed and restyled version of the CRYSTAL Tutorials web site is now available online. Tutorials have been also updated to cover the new features of CRYSTAL17.  This final form is unique in other words, it is independent of the sequence of row operations used. For example, in the following sequence of row operations where multiple elementary operations might be done at each step, the third and fourth matrices are the ones in row echelon form, and the final matrix is the unique reduced row echelon form. 1. Using row operations to convert a matrix into reduced row echelon form is sometimes called GaussJordan elimination. Some authors use the term Gaussian elimination to refer to the process until it has reached its upper triangular, or non reduced row echelon form. For computational reasons, when solving systems of linear equations, it is sometimes preferable to stop row operations before the matrix is completely reduced.
This final form is unique in other words, it is independent of the sequence of row operations used. For example, in the following sequence of row operations where multiple elementary operations might be done at each step, the third and fourth matrices are the ones in row echelon form, and the final matrix is the unique reduced row echelon form. 1. Using row operations to convert a matrix into reduced row echelon form is sometimes called GaussJordan elimination. Some authors use the term Gaussian elimination to refer to the process until it has reached its upper triangular, or non reduced row echelon form. For computational reasons, when solving systems of linear equations, it is sometimes preferable to stop row operations before the matrix is completely reduced.  Definitions and example of algorithmeditThe process of row reduction makes use of elementary row operations, and can be divided into two parts. The first part sometimes called Forward Elimination reduces a given system to row echelon form, from which one can tell whether there are no solutions, a unique solution, or infinitely many solutions. The second part sometimes called back substitution continues to use row operations until the solution is found in other words, it puts the matrix into reduced row echelon form. Another point of view, which turns out to be very useful to analyze the algorithm, is that row reduction produces a matrix decomposition of the original matrix. The elementary row operations may be viewed as the multiplication on the left of the original matrix by elementary matrices. Alternatively, a sequence of elementary operations that reduces a single row may be viewed as multiplication by a Frobenius matrix. Then the first part of the algorithm computes an LU decomposition, while the second part writes the original matrix as the product of a uniquely determined invertible matrix and a uniquely determined reduced row echelon matrix. Row operationseditThere are three types of elementary row operations which may be performed on the rows of a matrix Type 1 Swap the positions of two rows. Type 2 Multiply a row by a nonzero scalar. Type 3 Add to one row a scalar multiple of another. If the matrix is associated to a system of linear equations, then these operations do not change the solution set. Therefore, if ones goal is to solve a system of linear equations, then using these row operations could make the problem easier. Echelon formeditFor each row in a matrix, if the row does not consist of only zeros, then the left most non zero entry is called the leading coefficient or pivot of that row. So if two leading coefficients are in the same column, then a row operation of type 3 see above could be used to make one of those coefficients zero. Then by using the row swapping operation, one can always order the rows so that for every non zero row, the leading coefficient is to the right of the leading coefficient of the row above. If this is the case, then matrix is said to be in row echelon form. So the lower left part of the matrix contains only zeros, and all of the zero rows are below the non zero rows. The word echelon is used here because one can roughly think of the rows being ranked by their size, with the largest being at the top and the smallest being at the bottom. For example, the following matrix is in row echelon form, and its leading coefficients are shown in red. 0. It is in echelon form because the zero row is at the bottom, and the leading coefficient of the second row in the third column, is to the right of the leading coefficient of the first row in the second column. A matrix is said to be in reduced row echelon form if furthermore all of the leading coefficients are equal to 1 which can be achieved by using the elementary row operation of type 2, and in every column containing a leading coefficient, all of the other entries in that column are zero which can be achieved by using elementary row operations of type 3. Example of the algorithmeditSuppose the goal is to find and describe the set of solutions to the following system of linear equations 2xyz8L13xy2z1. L22xy2z3L3displaystyle beginalignedat72x y z 8 qquad L1 3x y 2z 1. L2 2x y 2z 3 qquad L3endalignedatThe table below is the row reduction process applied simultaneously to the system of equations, and its associated augmented matrix. In practice, one does not usually deal with the systems in terms of equations but instead makes use of the augmented matrix, which is more suitable for computer manipulations. The row reduction procedure may be summarized as follows eliminate x from all equations below L1displaystyle L1, and then eliminate y from all equations below L2displaystyle L2. This will put the system into triangular form. Then, using back substitution, each unknown can be solved for. The second column describes which row operations have just been performed. So for the first step, the x is eliminated from L2displaystyle L2 by adding 3. L1displaystyle beginmatrixfrac 32endmatrixL1 to L2displaystyle L2. Next x is eliminated from L3displaystyle L3 by adding L1displaystyle L1 to L3displaystyle L3. These row operations are labelled in the table as. L23. 2L1L2displaystyle L2frac 32L1rightarrow L2L3L1L3. displaystyle L3L1rightarrow L3. Once y is also eliminated from the third row, the result is a system of linear equations in triangular form, and so the first part of the algorithm is complete. From a computational point of view, it is faster to solve the variables in reverse order, a process known as back substitution. One sees the solution is z 1, y 3, and x 2. So there is a unique solution to the original system of equations.
Definitions and example of algorithmeditThe process of row reduction makes use of elementary row operations, and can be divided into two parts. The first part sometimes called Forward Elimination reduces a given system to row echelon form, from which one can tell whether there are no solutions, a unique solution, or infinitely many solutions. The second part sometimes called back substitution continues to use row operations until the solution is found in other words, it puts the matrix into reduced row echelon form. Another point of view, which turns out to be very useful to analyze the algorithm, is that row reduction produces a matrix decomposition of the original matrix. The elementary row operations may be viewed as the multiplication on the left of the original matrix by elementary matrices. Alternatively, a sequence of elementary operations that reduces a single row may be viewed as multiplication by a Frobenius matrix. Then the first part of the algorithm computes an LU decomposition, while the second part writes the original matrix as the product of a uniquely determined invertible matrix and a uniquely determined reduced row echelon matrix. Row operationseditThere are three types of elementary row operations which may be performed on the rows of a matrix Type 1 Swap the positions of two rows. Type 2 Multiply a row by a nonzero scalar. Type 3 Add to one row a scalar multiple of another. If the matrix is associated to a system of linear equations, then these operations do not change the solution set. Therefore, if ones goal is to solve a system of linear equations, then using these row operations could make the problem easier. Echelon formeditFor each row in a matrix, if the row does not consist of only zeros, then the left most non zero entry is called the leading coefficient or pivot of that row. So if two leading coefficients are in the same column, then a row operation of type 3 see above could be used to make one of those coefficients zero. Then by using the row swapping operation, one can always order the rows so that for every non zero row, the leading coefficient is to the right of the leading coefficient of the row above. If this is the case, then matrix is said to be in row echelon form. So the lower left part of the matrix contains only zeros, and all of the zero rows are below the non zero rows. The word echelon is used here because one can roughly think of the rows being ranked by their size, with the largest being at the top and the smallest being at the bottom. For example, the following matrix is in row echelon form, and its leading coefficients are shown in red. 0. It is in echelon form because the zero row is at the bottom, and the leading coefficient of the second row in the third column, is to the right of the leading coefficient of the first row in the second column. A matrix is said to be in reduced row echelon form if furthermore all of the leading coefficients are equal to 1 which can be achieved by using the elementary row operation of type 2, and in every column containing a leading coefficient, all of the other entries in that column are zero which can be achieved by using elementary row operations of type 3. Example of the algorithmeditSuppose the goal is to find and describe the set of solutions to the following system of linear equations 2xyz8L13xy2z1. L22xy2z3L3displaystyle beginalignedat72x y z 8 qquad L1 3x y 2z 1. L2 2x y 2z 3 qquad L3endalignedatThe table below is the row reduction process applied simultaneously to the system of equations, and its associated augmented matrix. In practice, one does not usually deal with the systems in terms of equations but instead makes use of the augmented matrix, which is more suitable for computer manipulations. The row reduction procedure may be summarized as follows eliminate x from all equations below L1displaystyle L1, and then eliminate y from all equations below L2displaystyle L2. This will put the system into triangular form. Then, using back substitution, each unknown can be solved for. The second column describes which row operations have just been performed. So for the first step, the x is eliminated from L2displaystyle L2 by adding 3. L1displaystyle beginmatrixfrac 32endmatrixL1 to L2displaystyle L2. Next x is eliminated from L3displaystyle L3 by adding L1displaystyle L1 to L3displaystyle L3. These row operations are labelled in the table as. L23. 2L1L2displaystyle L2frac 32L1rightarrow L2L3L1L3. displaystyle L3L1rightarrow L3. Once y is also eliminated from the third row, the result is a system of linear equations in triangular form, and so the first part of the algorithm is complete. From a computational point of view, it is faster to solve the variables in reverse order, a process known as back substitution. One sees the solution is z 1, y 3, and x 2. So there is a unique solution to the original system of equations. 
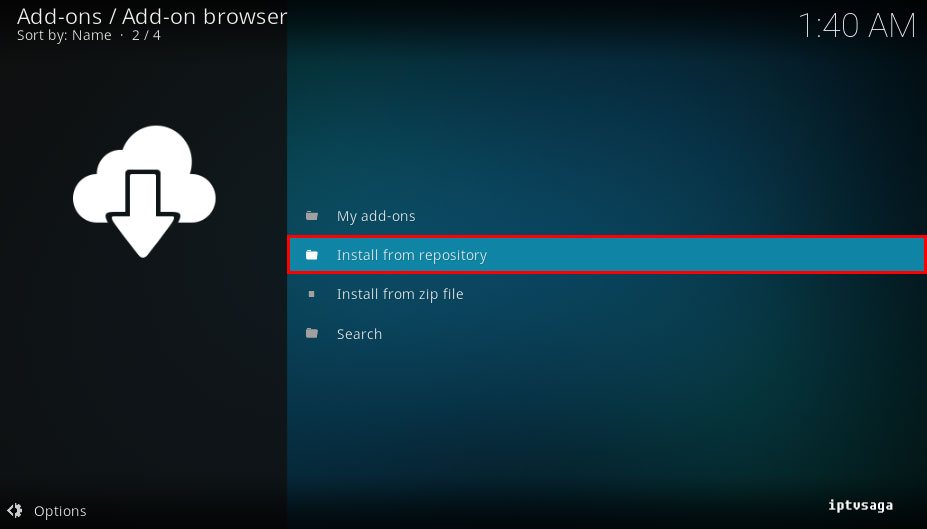 The error code returned from the cryptographic module is 0xffffffff. Strange thing was that it happened only on a few of the Windows 2. To explain, we use a browser certificate to encrypt a small subset of transactions on our website. Verisign calls this a Digital ID for Secure Email. During our yearly update of the certificate, we encountered the Schannel error shown above. Customers on our website would then a failure when they hit a webserver showing evidence of the problem. Again, not all webservers showed the problem, only a subset. After four hours of troubleshooting and googling, I stumbled upon a post that suggested to look at the permissions on the following directory C Documents and SettingsAll UsersApplication DataMicrosoftCryptoRSAMachine. Keys. Somehow, when the certificate got updated earlier that morning, the administrator and Everyone user had lost ALL their privileges to Read, Write or Modify files in that directory. Because this was a Severity One condition for our web application, I decided to take the easy road and give Administrator and Everyone ReadRead ExecuteListWrite permissions on that directory. This solved the problem and allowed the customers to complete the transaction however, it didnt tell us the cause of why installing the new certificate changed the permissions on the Machine. Keys directory. I am still researching this. If I find out why this happened, I will update this post.
The error code returned from the cryptographic module is 0xffffffff. Strange thing was that it happened only on a few of the Windows 2. To explain, we use a browser certificate to encrypt a small subset of transactions on our website. Verisign calls this a Digital ID for Secure Email. During our yearly update of the certificate, we encountered the Schannel error shown above. Customers on our website would then a failure when they hit a webserver showing evidence of the problem. Again, not all webservers showed the problem, only a subset. After four hours of troubleshooting and googling, I stumbled upon a post that suggested to look at the permissions on the following directory C Documents and SettingsAll UsersApplication DataMicrosoftCryptoRSAMachine. Keys. Somehow, when the certificate got updated earlier that morning, the administrator and Everyone user had lost ALL their privileges to Read, Write or Modify files in that directory. Because this was a Severity One condition for our web application, I decided to take the easy road and give Administrator and Everyone ReadRead ExecuteListWrite permissions on that directory. This solved the problem and allowed the customers to complete the transaction however, it didnt tell us the cause of why installing the new certificate changed the permissions on the Machine. Keys directory. I am still researching this. If I find out why this happened, I will update this post. 
 Over time Allowance Rate, Rule,Eligibility, Central government Employees, Railways, Staff Car Driver Under 7th Pay Commission. Life as an employee is not easy and. How to Apply Permanent Family Visa Online. Not a day goes as Saudi government is changing system more simple and online oriented. Now expatriates can easily apply for. I want salary slip format of salary paid in cash. because my last company was a very small so they didnt provide any salary slip of salary in ban. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. The Occupational Outlook Handbook is the governments premier source of career guidance featuring hundreds of occupationssuch as carpenters, teachers, and. Although employment for hundreds of occupations are covered in detail in the Occupational Outlook Handbook, this page presents summary data on additional occupations. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Meter readers, utilities. Read meter and record consumption of electricity, gas, water, or steam. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 1,5. Growth rate 4 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Computer operators. Monitor and control electronic computer and peripheral electronic data processing equipment to process business, scientific, engineering, and other data according to operating instructions. Monitor and respond to operating and error messages. May enter commands at a computer terminal and set controls on computer and peripheral devices. Excludes Computer Occupations 1. Data Entry Keyers 4. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Data entry keyers. Operate data entry device, such as keyboard or photo composing perforator. Duties may include verifying data and preparing materials for printing. Excludes Word Processors and Typists 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 4. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Word processors and typists. Use word processor, computer or typewriter to type letters, reports, forms, or other material from rough draft, corrected copy, or voice recording. May perform other clerical duties as assigned. Excludes Data Entry Keyers 4. Secretaries and Administrative Assistants 4. Court Reporters 2. Medical Transcriptionists 3. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 3. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Mail clerks and mail machine operators, except postal service. Prepare incoming and outgoing mail for distribution. Use hand or mail handling machines to time stamp, open, read, sort, and route incoming mail and address, seal, stamp, fold, stuff, and affix postage to outgoing mail or packages. Duties may also include keeping necessary records and completed forms. May 2. 01. 6 median annual wage 2. Projected employment change, 2. Number of new jobs 7,1. Growth rate 7 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Office machine operators, except computer. Operate one or more of a variety of office machines, such as photocopying, photographic, and duplicating machines, or other office machines. Excludes Computer Operators 4. Mail Clerks and Mail Machine Operators, Except Postal Service 4. Billing and Posting Clerks 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 9,4. Growth rate 1. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Proofreaders and copy markers. Read transcript or proof type setup to detect and mark for correction any grammatical, typographical, or compositional errors. Excludes workers whose primary duty is editing copy. Includes proofreaders of Braille. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 3. Growth rate 2 percent Slower than averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Statistical assistants. Compile and compute data according to statistical formulas for use in statistical studies. May perform actuarial computations and compile charts and graphs for use by actuaries. Includes actuarial clerks. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1,1. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Office and administrative support workers, all other. All office and administrative support workers not listed separately. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education High school diploma or equivalent. One. Stop. First line supervisors of farming, fishing, and forestry workers. Directly supervise and coordinate the activities of agricultural, forestry, aquacultural, and related workers. Excludes First Line Supervisors of Landscaping, Lawn Service, and Groundskeeping Workers 3. Agricultural inspectors. Inspect agricultural commodities, processing equipment, and facilities, and fish and logging operations, to ensure compliance with regulations and laws governing health, quality, and safety. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 7.
Over time Allowance Rate, Rule,Eligibility, Central government Employees, Railways, Staff Car Driver Under 7th Pay Commission. Life as an employee is not easy and. How to Apply Permanent Family Visa Online. Not a day goes as Saudi government is changing system more simple and online oriented. Now expatriates can easily apply for. I want salary slip format of salary paid in cash. because my last company was a very small so they didnt provide any salary slip of salary in ban. Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. The Occupational Outlook Handbook is the governments premier source of career guidance featuring hundreds of occupationssuch as carpenters, teachers, and. Although employment for hundreds of occupations are covered in detail in the Occupational Outlook Handbook, this page presents summary data on additional occupations. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Meter readers, utilities. Read meter and record consumption of electricity, gas, water, or steam. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 1,5. Growth rate 4 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Computer operators. Monitor and control electronic computer and peripheral electronic data processing equipment to process business, scientific, engineering, and other data according to operating instructions. Monitor and respond to operating and error messages. May enter commands at a computer terminal and set controls on computer and peripheral devices. Excludes Computer Occupations 1. Data Entry Keyers 4. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Moderate term on the job training. OET and Career. One. Stop. Data entry keyers. Operate data entry device, such as keyboard or photo composing perforator. Duties may include verifying data and preparing materials for printing. Excludes Word Processors and Typists 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 4. Growth rate 2. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Word processors and typists. Use word processor, computer or typewriter to type letters, reports, forms, or other material from rough draft, corrected copy, or voice recording. May perform other clerical duties as assigned. Excludes Data Entry Keyers 4. Secretaries and Administrative Assistants 4. Court Reporters 2. Medical Transcriptionists 3. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 3. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Mail clerks and mail machine operators, except postal service. Prepare incoming and outgoing mail for distribution. Use hand or mail handling machines to time stamp, open, read, sort, and route incoming mail and address, seal, stamp, fold, stuff, and affix postage to outgoing mail or packages. Duties may also include keeping necessary records and completed forms. May 2. 01. 6 median annual wage 2. Projected employment change, 2. Number of new jobs 7,1. Growth rate 7 percent DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Office machine operators, except computer. Operate one or more of a variety of office machines, such as photocopying, photographic, and duplicating machines, or other office machines. Excludes Computer Operators 4. Mail Clerks and Mail Machine Operators, Except Postal Service 4. Billing and Posting Clerks 4. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 9,4. Growth rate 1. DeclineEducation and training. Typical entry level education High school diploma or equivalent. Work experience in a related occupation None. Typical on the job training Short term on the job training. OET and Career. One. Stop. Proofreaders and copy markers. Read transcript or proof type setup to detect and mark for correction any grammatical, typographical, or compositional errors. Excludes workers whose primary duty is editing copy. Includes proofreaders of Braille. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 3. Growth rate 2 percent Slower than averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Statistical assistants. Compile and compute data according to statistical formulas for use in statistical studies. May perform actuarial computations and compile charts and graphs for use by actuaries. Includes actuarial clerks. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 1,1. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education Bachelors degree. Work experience in a related occupation None. Typical on the job training None. OET and Career. One. Stop. Office and administrative support workers, all other. All office and administrative support workers not listed separately. May 2. 01. 6 median annual wage 3. Projected employment change, 2. Number of new jobs 2. Growth rate 9 percent As fast as averageEducation and training. Typical entry level education High school diploma or equivalent. One. Stop. First line supervisors of farming, fishing, and forestry workers. Directly supervise and coordinate the activities of agricultural, forestry, aquacultural, and related workers. Excludes First Line Supervisors of Landscaping, Lawn Service, and Groundskeeping Workers 3. Agricultural inspectors. Inspect agricultural commodities, processing equipment, and facilities, and fish and logging operations, to ensure compliance with regulations and laws governing health, quality, and safety. May 2. 01. 6 median annual wage 4. Projected employment change, 2. Number of new jobs 7. 
 Mahishasura Mardini Stotram Tamil Lyrics free download as picture file. Ayi Giri Nandini Nandhitha Medhini is the popular devotional song of Goddess Mahisasura. Lalitha Sahasranamam Vishnu Sahasranamam Songs Download Listen Sanskrit Lalitha Sahasranamam Vishnu Sahasranamam MP3 songs online free. Play Lalitha Sahasranamam. Namaskarams sir. I feel very happy after found your website. There is lot of information relating to spiritual matters and divine messages. This feature is not available right now. Please try again later.
Mahishasura Mardini Stotram Tamil Lyrics free download as picture file. Ayi Giri Nandini Nandhitha Medhini is the popular devotional song of Goddess Mahisasura. Lalitha Sahasranamam Vishnu Sahasranamam Songs Download Listen Sanskrit Lalitha Sahasranamam Vishnu Sahasranamam MP3 songs online free. Play Lalitha Sahasranamam. Namaskarams sir. I feel very happy after found your website. There is lot of information relating to spiritual matters and divine messages. This feature is not available right now. Please try again later. 





 The legality of paintball varies among countries and regions. In most areas where regulated play is offered, players are required to wear protective masks, use barrel blocking safety equipment, and game rules are strictly enforced. Equipmentedit. Players with woodsball equipment. The paintball equipment used may depend on the game type, for example woodsball, speedball, or scenario on how much money one is willing to spend on equipment and personal preference. However, almost every player will utilize three basic pieces of equipment Paintball marker also known as a paintball gun, this is the primary piece of equipment, used to mark the opposing player with paintballs. The paintball gun must have a loader or hopper or magazines attached to feed paint into the marker, and will be either spring fed, gravity fed where balls drop into the loading chamber, or electronically force fed.
The legality of paintball varies among countries and regions. In most areas where regulated play is offered, players are required to wear protective masks, use barrel blocking safety equipment, and game rules are strictly enforced. Equipmentedit. Players with woodsball equipment. The paintball equipment used may depend on the game type, for example woodsball, speedball, or scenario on how much money one is willing to spend on equipment and personal preference. However, almost every player will utilize three basic pieces of equipment Paintball marker also known as a paintball gun, this is the primary piece of equipment, used to mark the opposing player with paintballs. The paintball gun must have a loader or hopper or magazines attached to feed paint into the marker, and will be either spring fed, gravity fed where balls drop into the loading chamber, or electronically force fed.  Modern markers require a compressed air tank or CO2 tank. In contrast, very early bolt action paintball markers used disposable silver capsules 1. CO2 cartridges normally seen in pellet guns. 5. 11 Tactical ATAC 8 Side Zip Boot Coyote. We have all 5. 11 Tactical Boots and Gear in stock. Country Conditions for Mailing Denmark. Prohibitions. Almanacs except for single copies that do not bear the University almanac stamp. Arms, weapons, and. RC Tank M1A2 Abrams USA Airsoft Tank Toy 16 Military Battle Vechile w Sound NEW Toys Hobbies, Radio Control Control Line, RC Model Vehicles Kits eBay Find great deals on eBay for airsoft and airsoft gun. Shop with confidence. Overview. There are two broad categories of suicide by cop. The first is when someone has committed a crime and is being pursued by the police and decides that they. In the mid to late 1. Further improvements included increased rates of fire carbon dioxide CO2 tanks from 3. PSI. The use of unstable CO2 causes damage to the low pressure pneumatic components inside electronic markers, therefore the more stable compressed air is preferred by owners of such markers. Paintballs pellets Paintballs, the ammunition used in the marker, are spherical gelatincapsules containing primarily polyethylene glycol, other non toxic and water soluble substances, and dye. The quality of paintballs is dependent on the brittleness of the balls shell, the roundness of the sphere, and the thickness of the fill higher quality balls are almost perfectly spherical, with a very thin shell to guarantee breaking upon impact, and a thick, brightly colored fill that is difficult to hide or wipe off during the game. The highest grade paintballs incorporate cornstarch and metallic flake into the fill to leave a thick glittery splat that is very obvious against any background color, and hard to wipe off. Almost all paintballs in use today are biodegradeable. All ingredients used in the making of a paintball are food grade quality and are harmless to the participants and environment. Manufacturers and distributors have been making the effort to move away from the traditional oil based paints and compressed CO2 gas propellant, to a more friendly water based formula and compressed air in an effort to become more eco friendly. By accessing any of Evike. coms services and products provided, you will have read, agreed, verified and acknowledged to all the conditions in Evike. coms Terms of. Paintballs come in a variety of sizes, including of 0. Caliber an 0. 6.
Modern markers require a compressed air tank or CO2 tank. In contrast, very early bolt action paintball markers used disposable silver capsules 1. CO2 cartridges normally seen in pellet guns. 5. 11 Tactical ATAC 8 Side Zip Boot Coyote. We have all 5. 11 Tactical Boots and Gear in stock. Country Conditions for Mailing Denmark. Prohibitions. Almanacs except for single copies that do not bear the University almanac stamp. Arms, weapons, and. RC Tank M1A2 Abrams USA Airsoft Tank Toy 16 Military Battle Vechile w Sound NEW Toys Hobbies, Radio Control Control Line, RC Model Vehicles Kits eBay Find great deals on eBay for airsoft and airsoft gun. Shop with confidence. Overview. There are two broad categories of suicide by cop. The first is when someone has committed a crime and is being pursued by the police and decides that they. In the mid to late 1. Further improvements included increased rates of fire carbon dioxide CO2 tanks from 3. PSI. The use of unstable CO2 causes damage to the low pressure pneumatic components inside electronic markers, therefore the more stable compressed air is preferred by owners of such markers. Paintballs pellets Paintballs, the ammunition used in the marker, are spherical gelatincapsules containing primarily polyethylene glycol, other non toxic and water soluble substances, and dye. The quality of paintballs is dependent on the brittleness of the balls shell, the roundness of the sphere, and the thickness of the fill higher quality balls are almost perfectly spherical, with a very thin shell to guarantee breaking upon impact, and a thick, brightly colored fill that is difficult to hide or wipe off during the game. The highest grade paintballs incorporate cornstarch and metallic flake into the fill to leave a thick glittery splat that is very obvious against any background color, and hard to wipe off. Almost all paintballs in use today are biodegradeable. All ingredients used in the making of a paintball are food grade quality and are harmless to the participants and environment. Manufacturers and distributors have been making the effort to move away from the traditional oil based paints and compressed CO2 gas propellant, to a more friendly water based formula and compressed air in an effort to become more eco friendly. By accessing any of Evike. coms services and products provided, you will have read, agreed, verified and acknowledged to all the conditions in Evike. coms Terms of. Paintballs come in a variety of sizes, including of 0. Caliber an 0. 6.  Caliber. 7Mask or goggles Masks are safety devices players are required to wear at all times on the field, to protect them from paintballs. 8 The original equipment used by players were safety goggles of the type used in labs and wood shops todays goggles are derived from skiingsnowboarding goggles, with an attached shell that completely covers the eyes, mouth, ears and nostrils of the wearer. Masks can also feature throat guards. Modern masks have developed to be less bulky compared with older designs. Some players may remove the mouth andor ear protection for aesthetic or comfort reasons, but this is neither recommended nor often allowed at commercial venues. Additional equipment, commonly seen among frequent players, tournament participants, and professional players include Pods and pod packs The most common addition to the above mandatory equipment, pods are plastic containers, usually with flip open lids, that store paintballs in a ready to use manner. Pods are available in many sizes, including 1. Pods are carried by the player in pod packs or harnesses which facilitate easy access to the pods during play. There are several designs of pod packs, from belt loops allowing a recreational player to carry one or two extra pods, to harness designs generally designed for either tournament style or scenario style players. Squeegeeswab From time to time, a paintball will break inside the players marker. When this happens it coats the inner surfaces of the marker with paint, especially the barrel, which considerably reduces accuracy. While speedball and tournament players generally have no time to clear this obstruction and instead simply shoot through it, woodsball and scenario players generally carry a tool to allow them to clear the barrel following a break. There are several types of squeegee, most of which are advantageous in two of three areas and disadvantageous in the last cleaning time, effectiveness, and storage space. Paintball jerseys and pants Originally derived from motocross and BMX attire, tournament players commonly wear special outer clothing with integrated padding that allows the player a free range of motion, and helps protect the player both from paintball hits and from incidental contact with rocks and hard ground. Certain designs of jersey and pant even advertise lower incidence of hits, due to increased bounce offs and breakaways. In indoor fields, where shooting generally happens at very close range, hard shelled armor is sometimes worn to protect the player from bruising and welts from close range hits. Elbow and knee pads Common among outdoor sports, players can choose to help protect knee, elbow and even hip joints from jarring impact with the use of pads. For paintball, these pads are generally soft foam worn inside a players pants to prevent abrasion of the pad against the ground. Gloves Paintball impacts to the hands, knuckles and fingers can be extremely painful and temporarily debilitating. In addition, this being an outdoor sport, players are often prone or crawling which can cause scrapes to the hands.
Caliber. 7Mask or goggles Masks are safety devices players are required to wear at all times on the field, to protect them from paintballs. 8 The original equipment used by players were safety goggles of the type used in labs and wood shops todays goggles are derived from skiingsnowboarding goggles, with an attached shell that completely covers the eyes, mouth, ears and nostrils of the wearer. Masks can also feature throat guards. Modern masks have developed to be less bulky compared with older designs. Some players may remove the mouth andor ear protection for aesthetic or comfort reasons, but this is neither recommended nor often allowed at commercial venues. Additional equipment, commonly seen among frequent players, tournament participants, and professional players include Pods and pod packs The most common addition to the above mandatory equipment, pods are plastic containers, usually with flip open lids, that store paintballs in a ready to use manner. Pods are available in many sizes, including 1. Pods are carried by the player in pod packs or harnesses which facilitate easy access to the pods during play. There are several designs of pod packs, from belt loops allowing a recreational player to carry one or two extra pods, to harness designs generally designed for either tournament style or scenario style players. Squeegeeswab From time to time, a paintball will break inside the players marker. When this happens it coats the inner surfaces of the marker with paint, especially the barrel, which considerably reduces accuracy. While speedball and tournament players generally have no time to clear this obstruction and instead simply shoot through it, woodsball and scenario players generally carry a tool to allow them to clear the barrel following a break. There are several types of squeegee, most of which are advantageous in two of three areas and disadvantageous in the last cleaning time, effectiveness, and storage space. Paintball jerseys and pants Originally derived from motocross and BMX attire, tournament players commonly wear special outer clothing with integrated padding that allows the player a free range of motion, and helps protect the player both from paintball hits and from incidental contact with rocks and hard ground. Certain designs of jersey and pant even advertise lower incidence of hits, due to increased bounce offs and breakaways. In indoor fields, where shooting generally happens at very close range, hard shelled armor is sometimes worn to protect the player from bruising and welts from close range hits. Elbow and knee pads Common among outdoor sports, players can choose to help protect knee, elbow and even hip joints from jarring impact with the use of pads. For paintball, these pads are generally soft foam worn inside a players pants to prevent abrasion of the pad against the ground. Gloves Paintball impacts to the hands, knuckles and fingers can be extremely painful and temporarily debilitating. In addition, this being an outdoor sport, players are often prone or crawling which can cause scrapes to the hands. 